 In today’s digital age, cybercriminals are always on the lookout for new ways to exploit unsuspecting users. One of the most common and effective cyber threats is phishing, and Apple device users are frequent targets. Whether you own an iPhone, iPad, Mac, or any other Apple product, it’s crucial to be aware of how phishing scams work and how to protect yourself from falling victim.
In today’s digital age, cybercriminals are always on the lookout for new ways to exploit unsuspecting users. One of the most common and effective cyber threats is phishing, and Apple device users are frequent targets. Whether you own an iPhone, iPad, Mac, or any other Apple product, it’s crucial to be aware of how phishing scams work and how to protect yourself from falling victim.
What Is Phishing?
Phishing is a type of cyber attack where scammers impersonate a trusted entity—such as Apple—to steal sensitive information like login credentials, credit card details, or personal data. These attacks often come in the form of deceptive emails, text messages, or fake websites designed to trick users into revealing their information.
Common Apple Phishing Scams
Apple users are particularly attractive targets for phishing attacks because they often store valuable data in their iCloud accounts. Here are some of the most common phishing scams aimed at Apple users:
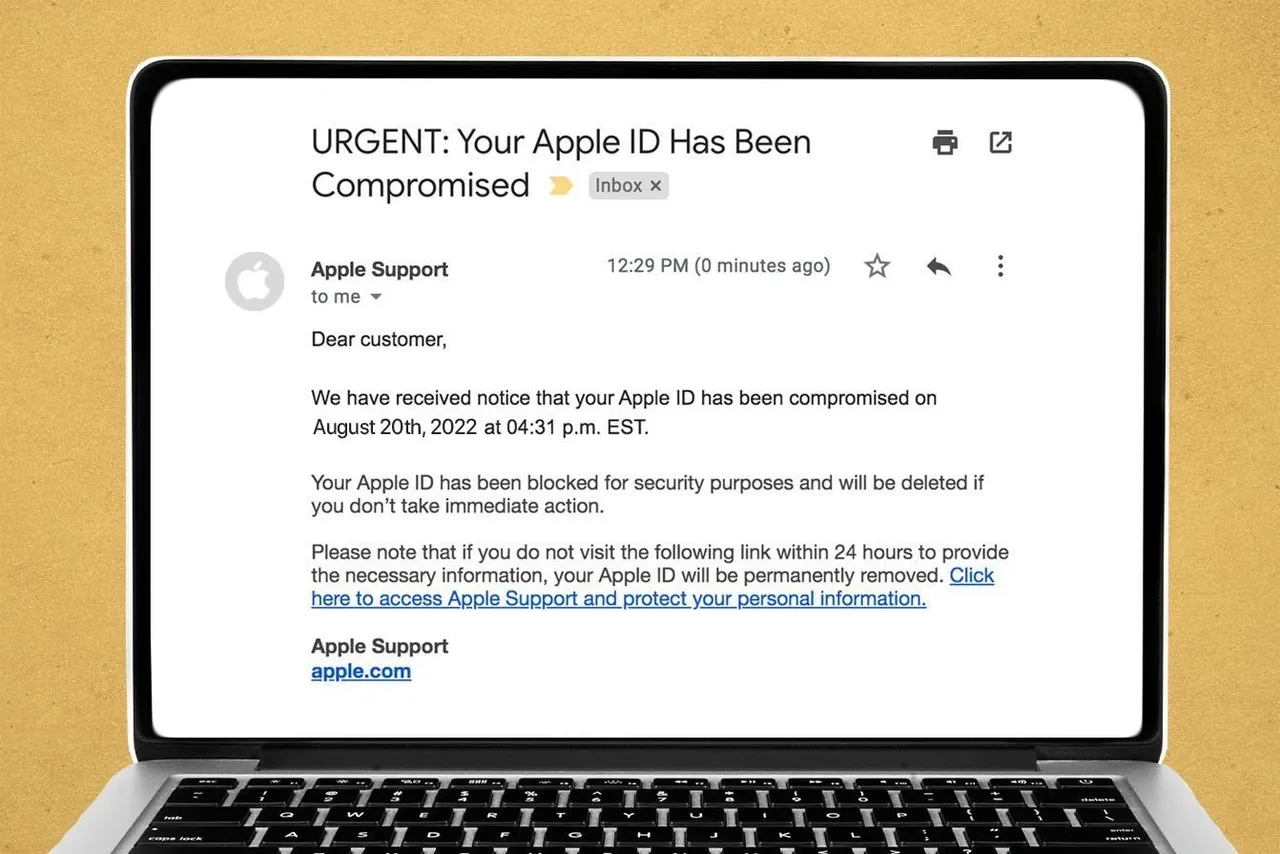
1. Fake Apple ID Login Requests
Cybercriminals send emails or text messages claiming that your Apple ID has been locked due to suspicious activity. These messages contain a link to a fraudulent website designed to look like Apple’s login page. If you enter your credentials, scammers can access your account, change your password, and lock you out.
2. iCloud Storage Expiry Scams
Scammers send emails warning that your iCloud storage is full or about to expire, urging you to upgrade immediately. The links in these messages lead to fake payment pages designed to steal your credit card information.
3. Fake Purchase Receipts
Some phishing emails claim that you have been charged for a purchase you didn’t make, prompting you to click a “cancel transaction” button. This link directs you to a fake Apple login page where scammers attempt to steal your credentials.
4. Apple Support Impersonation Calls
In this scam, fraudsters call or send messages pretending to be Apple Support, claiming that your account or device has been compromised. They then ask for your Apple ID credentials or even remote access to your device.
5. Gift Card Scams
Some scammers claim you need to pay a fee to unlock your Apple account or resolve a security issue. They may demand payment via Apple Gift Cards, a common trick used to extract money from victims.
How to Protect Yourself
Fortunately, there are several ways to safeguard yourself from Apple-related phishing scams:
- Verify Sender Information: Always check the sender’s email address or phone number. Apple’s official emails typically come from “@apple.com” target=”_blank”>”> Verify Sender Information: Always check the sender’s email address or phone number. Apple’s official emails typically come from “@apple.com.”
- Don’t Click Suspicious Links: If you receive an unexpected email or message urging you to log in or update your account, avoid clicking any links. Instead, visit Apple’s official website manually.
- Enable Two-Factor Authentication (2FA): This adds an extra layer of security to your Apple ID, making it harder for hackers to gain access.
- Beware of Urgent Requests: Scammers often use fear tactics, such as threats of account suspension. Stay calm and verify the message’s legitimacy before taking any action.
- Check for Typos and Poor Grammar: Phishing emails often contain spelling and grammatical errors, a red flag that the message isn’t from Apple.
- Report Suspicious Emails and Messages: Forward suspicious emails to [email protected]. If you receive a scam call, hang up immediately and report it to Apple.
Final Thoughts
Phishing scams are a growing threat, and Apple users need to stay vigilant. By being cautious, verifying communications, and following best security practices, you can protect your personal information from falling into the wrong hands. When in doubt, always visit Apple’s official website or contact Apple Support directly to confirm the legitimacy of any message or request.
Stay alert, stay informed, and stay secure!